

| Name | Description |
|---|---|
| Host | The URL or IP address of the LDAP server you want to talk to. Similar to the URL of a web site. |
| Port | The port number you are connecting to. The usual value is 389. (This is the also the default used by the class) |
| Domain |
Databases on the LDAP server side are organized by "domain". This
can be set to anything the administrator likes, it is not bound to a
web domain the company owns or anything like that. It may correspond
to the HOST address, but does not need to do so.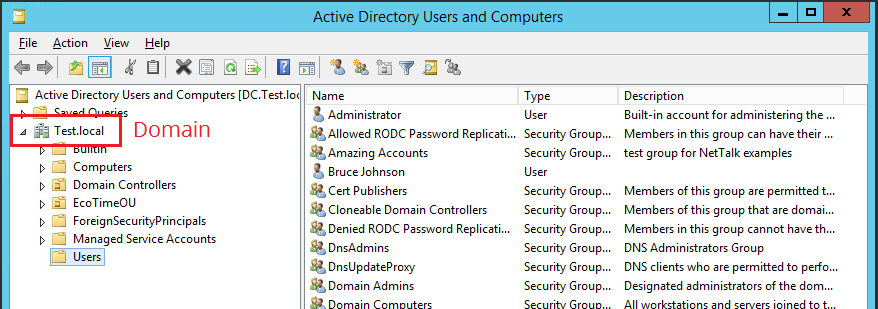
|
| Bind | When a client authenticates with a server this is known as Binding to the server. Typically this requires a valid user name, and password, to access the database, but some servers allow anonymous authentication. NetTalk uses two properties, AuthUser and AuthPassword to contain these items. Not that the user that is BINDed is purely for access to the database - they may be able to extract data from the database for other users in addition to themselves. |
| Attributes | These are like field names in a normal database. There are potentially a great many attributes assigned to an object. For example a user may have attributes like displayName, userPrincipalName, samAccountName, sn (for Surname) and so on. |
| cn CommonName | This is a property for each user, set by
the Administrator on the server. The Common Name is the whole name, as
displayed in the administrator panel below. (Notice also the Group
Name highlighted in the image below.) The Common Name of the highlighted user
is Wilson S. Demaggio. You do not change the Common Name by changing any of the properties of the user. (It _defaults_ to FirstName LastName, but changing those names does not change the common name.) To change the name right click on the list, and select the Rename option. 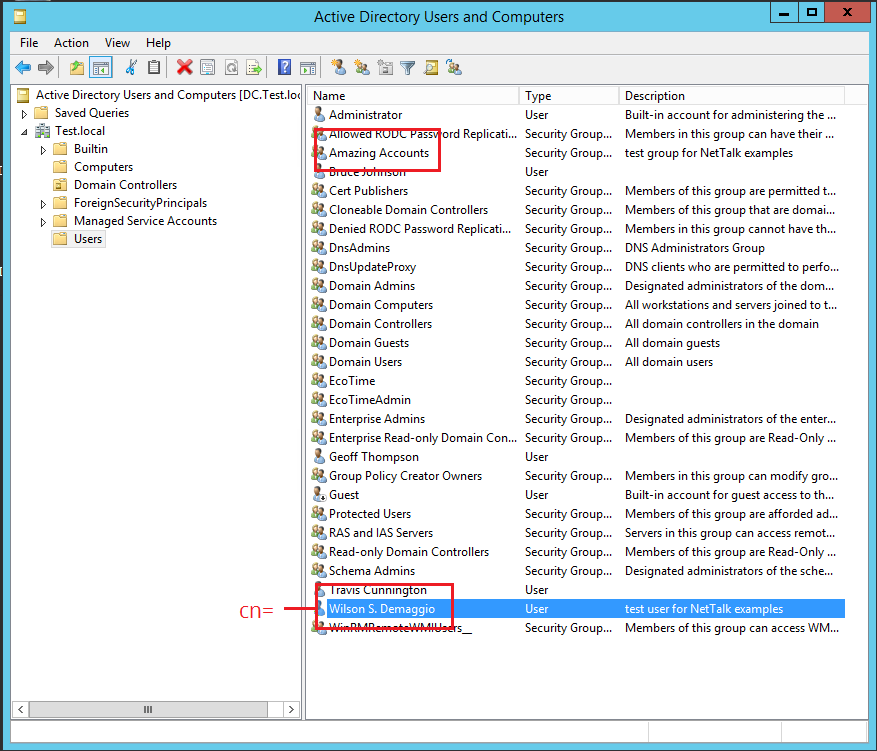 |
| Group name | The name of a Group in the directory. See the image above for an example of a group called Amazing Accounts. |
| User Logon Name UserPrincipalName sAMAccountName DisplayName | There are
four common login
approaches that are supported by the server. The first is the userPrincipalName, the second is the sAMAccountName and the third is by using the DisplayName. The more modern (and hence preferred) name is the userPrincipalName. The fourth approach is to accept the user logon name, and then internally the code uses the Domain to construct the UserPrincipalName from that. (For more on this see What to Use as the User Login.) The first option uses both the user login name, AND the domain. In the picture below, the userPrincipalName of this user is wilson@Test.local. The sAMAccount name is wilson, but the login would be TESTIRONMAN\wilson 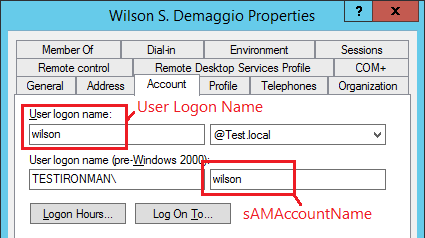
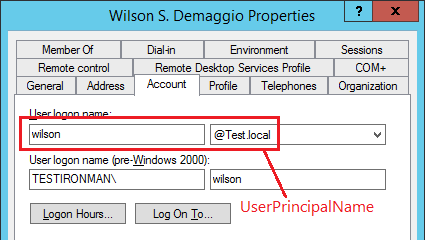
The Third approach uses the Display Name. This approach does not include the domain. This approach is not recommended because the display name does not have to be unique. So multiple users could end up with the same display name. If multiple users have the same name then NONE of them can login using this approach. 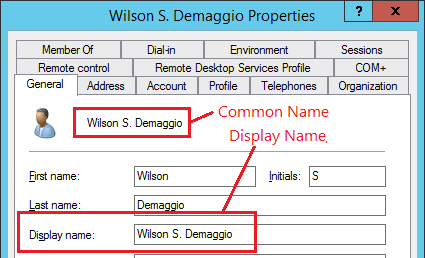
The Common Name is often the same as the Display Name, but they don't necessarily have to be the same. |
| userPrincipalName | This is the attribute name which holds the login. In the Active Directory Administrator this is referred to as the Logon Name, however when constructing User Filters the correct name of the attribute is userPrincipalName. |
| sAMAccountName | This is an older approach to logins. It
consists of the single-name domain, followed by a \ and the user
name. In the picture above this would be TESTIRONMAN\wilson |
| ou Organizational Unit |
This is like a group that is used to organize objects in the directory. In a large company this might be the users department. By default in Active Directory Directory Services there is an ou called Users. This may be required in the UserFilter. |
A good example of these features in action is in the \examples\nettalk\LDAP\ActiveDirectory folder.
| User filter | Attributes | Description |
|---|---|---|
| cn=Wilson S. Demaggio | distinguishedName,mail | Get the distinguisedName and mail attributes for this user. |
| cn=Wilson S. Demaggio | memberof | Returns a
string containing a list of the groups that the user is in. For
example CN=AmazingAccounts,CN=Users,DC=Test,DC=Local |
| cn=AmazingAccounts | member | Returns a queue of
users that are members of this group. Each line in the queue
contains the member information. For example CN=Wilson S. Demaggio,CN=Users,DC=Test,DC=local |
| cn=Wilson S. Demaggio | * | Gets all the attributes for a single user, as a queue. |
| objectClass=group | cn | Lists the common name for all the groups in the directory. |
| objectClass=group | distinguishedName | Lists the CN of each group, and also its location in the tree. |
| objectClass=group | cn,member | Lists the groups, and the direct members in each group |
| objectCategory=user | cn | Lists all the users in the directory |
| objectCategory=user | distinguishedName | Lists the CN of each user, and also their location in the tree. |
| &(objectclass=group)(cn=EcoTime) | cn,member | Lists the members in the group called EcoTime. |
| (&(objectClass=group)(member:1.2.840.113556.1.4.1941:=CN=Wilson
S. Demaggio,CN=Users,DC=Test,DC=local)) | cn | Lists all the groups that Wilson S. Demaggio is a member of. This is a recursive group search (ie supports groups in groups) and is Active Directory (2003 R2 and later) only. |
| Name | Type | Description |
|---|---|---|
| pHost | String | The URL or IP address of the LDAP server you are connecting to. |
| pPort | String | The port number of the LDAP server you are connecting to. Defaults to 389. |
| pAuthUser | String | The user name for the user when authenticating against the LDAP server. |
| pAuthPassword | String | The password for the user when authenticating against the LDAP server. |
| pDomain | String | The domain of the LDAP server. |
| pUser | String | A user filter. |
| pInGroup | String | A group name (used for UserInGroup method.) |
| pActiveDirectory | Long | New in Build 11.30. Set this if the server is Windows Server 2003 R2 or later. This will allow recursive group searches to be done. |
| Property | DDescription |
|---|---|
| ActiveDirectory | Set this to true if the LDAP server being used is an Active Directory server. Defaults to true. Allows for some "Active Directory Only" features to be used. Should only be set if the Active Directory Server is on Windows Server 2003 R2 or later. |
| AllowAnonymous | Set this to true if the LDAP server allows anonymous access. Usually the server does not allow anonymous access, and requires the AuthUser and AuthPassword properties to be set. |
| AttributesQueue | A Queue which holds the results of an attribute search. Populated after a call to GetAttributes. Can be inspected in the SearchDone method, after the parent call. |
| AuthPassword | The password, of the user who is requesting data from the server. |
| AuthUser | The login of the user who is requesting data from the server. |
| DebugPackets | If this is set to true then the contents of outgoing packets are sent to Debugview. Used for internal debugging only. |
| DistinguishedName | This is the Distinguished name of the user. Populate this using the GetDistinguishedName method. this field is auto-populated by a call to the UserInGroup method (if it's not already populated.) |
| Domain | The domain of the server that you are
connecting to. This is of the form
dc=test,dc=local It is set be a call to SetDomain. |
| DomainType | One of NetLDAP:UserPrincipalName,
NetLDAP:DisplayName,
NetLDAP:sAMAccountName. Defaults to NetLDAP:UserPricipalName. |
| Host | The IP address, or DNS name of the LDAP server machine. |
| LoginDomain | This is of the form
c.b.a, for example
test.local or
com.capesoft. It is set be a call to SetDomain. |
| Port | The Port of the LDAP server machine. The default port number is 389 for an unencrypted connection. For encrypted connections the port will likely be 636. |
| SearchPrefix | Allows the search for attributes, and users in a group, to be refined to a narrower scope. |
| User | The user being checked for the UserInGroup method. |
| UserIsInGroup | If the UserInGroup method is called, then the result can be tested in the Done method. |
| ValidUser | This is set to true if a request is made, and the AuthUser and AuthPassword properties are valid. If a Login is successful then the Done method will be called. |
| Method | Description |
|---|---|
| Done | This method is called when a request to the server has received a response. |
| ErrorTrap | This method is called if an error occurs while communicating with the server. |
| GetAttributes | Get attributes for a specific user. |
| GetAttributeValue | Reads an entry from the Attributes Queue after a call to GetAttributes. |
| MessageDone | |
| Search | Do an Addhoc search against the LDAP server. |
| SearchDone | Is called when the results of a search are available. |
| SetAttributesQueue | Set the Queue to receive the results from a call to GetAttributes. |
| SetAuthUser | Sets the AuthUser property, and possibly Domain property. |
| SetUser | Sets the User property |
| SetDomain | Sets the domain of the server that the program is connecting to. |
| Start | RReturns the object to a virgin state. |
| UserInGroup | Check to see if a specific user is in a Group or not. |
| ValidateUser | Validates the AuthUser and AuthPassword properties against the server, and allows other methods to execute. If another method is called before this method is called, then this method will be called automatically. |
| Parameter | DDescription |
|---|---|
| MessageID | The MessageID of the request which has just completed. |
| Parameter | DDescription |
|---|---|
| MessageId | The ID of the message being attempted. |
| ErrorCode | The NetTalk Error Code |
| Error | The NetTalk Error Message |
| Parameter | Description |
|---|---|
| User | A user filter to determine which user(s) to get the attribute(s) for. |
| Attributes | A comma delimited list of the attributes to fetch. If omitted (or blank) then all the attributes for the user are returned. |
| Parameter | Description |
|---|---|
| Attribute | The name of the attribute to read out the queue. This parameter is not case sensitive. |
| Instance | The instance number to retrieve. If this parameter is omitted then the first instance of the attribute in the queue is returned. |
| Parameter | Description |
|---|---|
| pBase | The root for the search. Most often contains a search prefix, and domain to search. |
| pFilter | The search term to search on. This filter is a User Filters. |
| pAttributes | The attributes to be included in the search result. This is a comma separated list. |
| pScope | The scope of the search. On of NetLDAP:SCOPE_BASEOBJECT, NetLDAP:SCOPE_ONELEVEL, NetLDAP:SCOPE_SUBTREE, NetLDAP:SCOPE_SUBORDINATE. If not sure try NetLDAP:SCOPE_SUBTREE. |
| pDerefAliases | One of NetLDAP:DEREF_NEVER, NetLDAP:DEREF_SEARCHING, NetLDAP:DEREF_FINDING, NetLDAP:DEREF_ALWAYS. If not sure try NetLDAP:DEREF_NEVER. |
| pSizeLimit | If omitted set to 0. The size limit of the response. If 0 then no limit is applied. |
| pTimeLimit | If omitted set to 0. The time limit for the search. If 0 then no limit is applied. |
| pTypesOnly | If omitted set to false. If true only types are included in the returned set. |
| Parameter | Description |
|---|---|
| MessageId | The MessageID of the request which has just completed. |
| ObjectName | The object name as returned by the server |
| pAttributes | The attribute list as returned by the server |
| Parameter | Description |
|---|---|
| AttributesQueue | The Queue to receive the results of a call to GetAttributes. |
| Parameter | Description |
|---|---|
| AuthUser | A user name. This may be a UserPrincipalName (of the format user@c.b.a), a sAMAccountName (of the form DOMAIN\USER), or a simple user displayName. |
| Type | If the preferred login type cannot
be auto-detected by the AuthUser (ie it does not
include an @ or \ or space symbol) then the type can be set
using this parameter. (This parameter is ignored if
the login type can be determined from the AuthUser). This parameter can be omitted or can be one of NetLDAP:UserPrincipalName, NetLDAP:samAccountName or NetLDAP:DisplayName. NetLDAP:UserPrincipalName is recommended. |
| Parameter | Description |
|---|---|
| Domain | The domain, on the LDAP (aka Active Directory) server, that you are connecting to. |
| Parameter | Description |
|---|---|
| User | If this already contains an
attribute=value form then the attribute part is
removed. If the value contains just a user id, then it is adjusted to an appropriate attribute=value form. Values containing an @ symbol are adjusted to userPrincipalName=user Values containing an \ symbol are adjusted to sAMAccountName=user Values containing a space are adjusted to displayName=user If none of these are detected then the login domain of the AuthUser (if it's been set) is used to create the userPrincipalName or samAccountName, based on the Type parameter, or failing that the AuthUser's type. |
| Type | If this is not set then the domain type of the AuthUser is used (if this parameter is used at all.) |
| Parameter | Description |
|---|---|
| User | A user filter to determine which user to check. If omitted then the current User property is used. (Typically as set by a call to SetUser) |
| Group | The name of the group to check. |
| ActiveDirectory | Set this to true if the LDAP server is a Windows Server 2003 R2 or later server. This switch defaults to false, and allows the class to use some Active-Directory-Only features. |